I have been working on a project lately called RAI. I am not going to talk about it here, but basically it is an external facing and internal facing application for one of the organisations I provide IT services for. For the external client we decided to use ADAM for the authentication source, so I started to have a look at using ADAM and the AD membership provider. Well lets just say that was 5 days I will never get back. So just in case you are ever in a situation where you need to get the AD membership provider to work with ADAM these are the step to installing ADAM so it is setup ready for you.
ADAM can be downloaded from Microsoft at
http://www.microsoft.com/downloads/details.aspx?FamilyId=9688F8B9-1034-4EF6-A3E5-2A2A57B5C8E4&displaylang=en#filelistThe following steps are required to install ADAM for use with the Active Directory .Net membership provider.
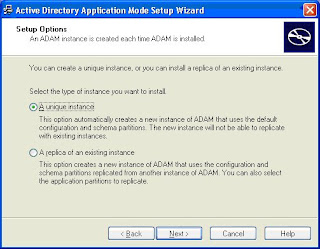
1. Run the ADAM installer.
2. Select “unique instance” , press next
3. Set the instance name to your project name in this case I am using “RAI” , press next
4. Set the LDAP port to 50000 and the SSL port to 50001 ,press next
5. Select “Yes, Create an application directory partition” and set the partition name to “O=[projectname]” , again in this case I use RAI press next.
6. Accept default or select a suitable place for the files , press next
7. Choose default for Service Account Selection
8. Choose "Currently logged on account" for ADAM Adminstrators
9. Import "MS-InetOrgPerson", "MS-User" and "MS-Userproxy"
10. Click next to complete the install
The ADAM instance for RAI will now be installed on the application server. It must now be configured.
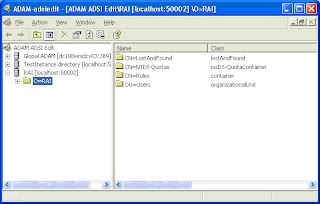
11. Open "ADAM ADSI Edit" from the ADAM program group in your start menu
12. Select "Action->Connect to..."
13. For name use your projectname
14. Alter the correct portnumber in the Port textbox (50000)
15. Change to “Well-Known naming context” and select “Schema” and then press OK
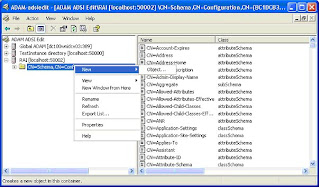
16. Right click on the schema item and select new object. From the class menu select “AttributeSchema”.
17. Create the following 5 new attribute schema entries
cn: PwdQuestion
OMSyntax: 64
lDAPDisplayName: PwdQuestion
isSingleValued: TRUE
AttributeSyntax: 2.5.5.12
AttributeID: 1.2.840.113556.1.6.1.1.6221
cn: PwdAnswer
OMSyntax: 64
lDAPDisplayName: PwdAnswer
isSingleValued: TRUE
AttributeSyntax: 2.5.5.12
AttributeID: 1.2.840.113556.1.6.1.1.6222
cn: FailedPwdCount
OMSyntax: 2
lDAPDisplayName: FailedPwdCount
isSingleValued: TRUE
AttributeSyntax: 2.5.5.9
AttributeID: 1.2.840.113556.1.6.1.1.6223
cn: FailedPwdAnswerTime
OMSyntax: 65
lDAPDisplayName: FailedPwdAnswerTime
isSingleValued: TRUE
AttributeSyntax: 2.5.5.16
AttributeID: 1.2.840.113556.1.6.1.1.6224
cn: FailedPwdLockOutTime
OMSyntax: 65
lDAPDisplayName: FailedPwdLockOutTime
isSingleValued: TRUE
AttributeSyntax: 2.5.5.16
AttributeID: 1.2.840.113556.1.6.1.1.6225
18. Close the "ADAM ADSIedit" program
19. The user schema object in the ADAM instance needs to be modified to support the additional attributes created in step 17. This needs to be done via the mmc ADAM snap-in. To create an MMC file for the ADAM Schema snap-in
20. From the taskbar Click Start, click Run, type mmc /a, and then click OK.
21. On the File menu, click Add/Remove Snap-in, and then click Add.
22. In Available Standalone Snap-ins, click ADAM Schema, click Add, click Close, and then click OK.
23. To connect to your ADAM instance through ADAM Schema, in the console tree, right-click ADAM Schema, click Change ADAM Server, and then complete the dialog box as follows
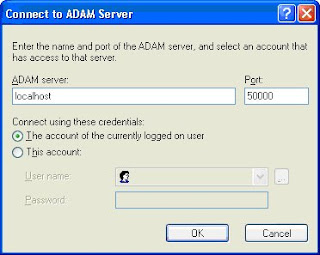
24. Click OK
25. In the left hand pane double click the “classes” folder to view the list of schema classes
26. Scroll down to “user” the user object and right click on it. Select properties and then select the attributes tab.
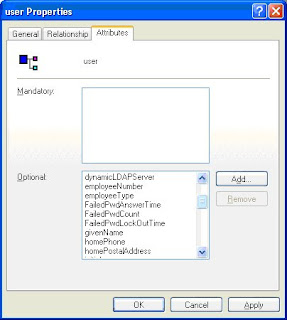
Add the five attributes create in step 21. cn: PwdQuestion , PwdAnswer, FailedPwdCount, FailedPwdAnswerTime, FailedPwdLockOutTime
27. Click OK and close the mmc console. The schema changes are complete. You must restart the ADAM service before you continue.
28. Open the windows services control panel from administrative tools and restart the ADAM service.
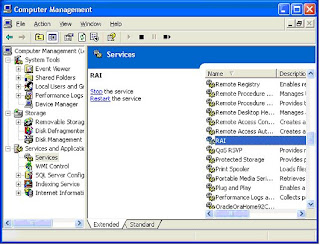
29. Close the services control panel.
30. Open the ADSI Edit tool again. Right Click on the [projectname] connection and select “settings”. Change the connection node to "Distinguished name" and enter “O=RAI”
31. Click "Ok"
32. Right-click the "O=RAI"-folder and select "New" and "Object..". Choose "organizationalUnit" and name it "Users", click next and then click finish.
33. Right-click the new "OU=Users"-folder and select "New" and "Object...". Select "user" and give the user the name "ADAMAdmin", click next and then click finish.
34. Right-click the "CN=ADAMAdmin" -account and choose "Reset password". Enter a password you will remember
35. Double-click the "CN=ADAMAdmin"-user and set the "msDS-UserAccountDisabled" to False , click ok and close the properties box.
36. Go to the "CN=Roles"-folder and double-click the "Administrators"-account. Locate the "member" attribute and double-click it. Choose "Add ADAM-account" and enter the distinguished name of your newly created user (CN=ADAMAdmin,OU=Users,O=RAI). Click the Ok-buttons to close the editor.
37. Right-click the root of the Connection in the left hand pane. Select “Settings” from the menu.
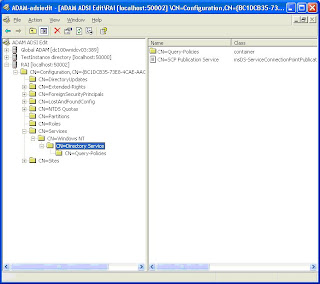
Change to “Well-Known naming context” and select “Configuration” and then press OK.
38. Navigate to CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,CN={GUID of the ADAM}.
39. Right-click CN=Directory Service and select Properties.
40. Double-click the dSHeuristics attribute.
41. Set the value to 0000000001001 and click OK.
42. Click OK to the CN=Directory Service properties box.
43. The ADAM configuration is now complete.
You will obviously need to setup your application web.config to use this ADAM instance. Have a look at http://authors.aspalliance.com/aspxtreme/sys/web/security/ActiveDirectoryMembershipProviderClass.aspx and http://msdn2.microsoft.com/en-us/library/ms998360.aspx for this information.







